According to PayScale, the typical annual cybersecurity wage of a penetration tester in the cloud security providers United States is $125,630, and in India, it is ₹2,151,258. A Security Architect is answerable for designing robust security structures which might be used to stop malware assaults. They carry out vulnerability exams and also provide technical help to the opposite safety team members.
Software Outlined Storage Greatest Practices

IBM Corporation, Cisco Systems, and others have been forging forward in the market with progressive cyber safety solutions based on cloud computing. These companies are designed on the Analytics as a Service (AaaS) platform, which helps customers in mitigating and figuring out threats. As the number, scope and scale of cyber attacks will increase, the demand for qualified cybersecurity professionals can additionally be on an upswing. Not only is the sector attention-grabbing and fulfilling, it offers numerous alternatives for profession growth, high rewards and the prospect to make an actual difference to organizations and industry.
What Number Of Cybersecurity Jobs Are There?
Malware varieties and capabilities are continuously evolving, which explains why extra organizations are falling victim to this risk. Worse, many firms are struggling to keep up with new and emerging forms of malware that spread quickly and are difficult to detect. They conduct community and methods analyses to determine and choose the most effective control mechanisms for the required security degree.
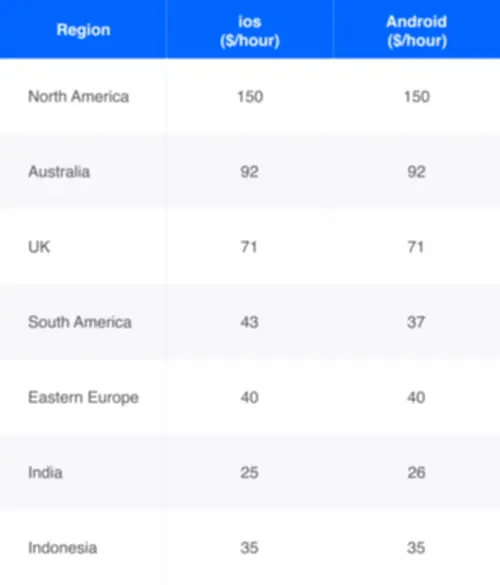
What’s The Cybersecurity Wage Per 30 Days In India?
In India, the sphere of cybersecurity is witnessing unprecedented growth, fueled by the digital transformation of businesses and an escalating wave of cyber threats. The salary dynamics in this subject are multifaceted, influenced by elements such as skill units, business verticals, geographical areas, demand-supply dynamics, and a dedication to steady studying. Cybersecurity professionals are liable for defending their company’s info and data from attacks by hackers, viruses, or other cyber threats. These professionals sometimes work in teams with other IT specialists, such as software builders or programmers.
What Corporations Would You’re Employed For?
- The company combines safety instruments and experts to leverage high-tech features, detect hackers and purge threats from techniques.
- A safety architect’s primary role is to evaluate systems, consider current security measures, and make recommendations to spice up security.
- By gaining a more detailed and holistic view of the threat landscape, firms can extra quickly understand threats and take steps to shut them down.
- An employer is primarily concerned with your foundational information, your lab/project experience, and the way properly you completed your degree program (i.e. have been you an ‘A’ scholar or ‘C’ student).
- Specialization could be a good factor in cybersecurity, with the likes of CrowdStrike, Okta, and OneTrust excessive on our record.
They monitor key methods, develop security patches, and deploy countermeasures in case of breaches. In this position, you also conduct penetration testing to determine laptop systems’ security. You may additionally create disaster restoration plans to help an organization get well after a cyberattack.
The Highest 5 Cybersecurity Firms In The Us

Teams looking for more flexibility can undertake RSA’s ID plus bundle, which is designed for guarding cloud and hybrid ecosystems with mobile and endpoint security features. Cymulate helps businesses bolster their cybersecurity defenses with simulation exams and automatic assessments that single out weaknesses in cloud environments and infrastructure. Businesses can then resolve tips on how to best allocate their sources to maximize their safety towards cyber threats.
In this case, you’ll reply to actual cyber assaults and should shield organizational sources from further damage. In this role, you should investigate and respond to cyber instances and gather intrusion proof, which might help catch perpetrators. In contrast, a cybersecurity engineer is on the advanced-level profession observe, so if you’re thinking about a profession as such, you should know that over 80% of job openings require greater schooling.
The firm says organizations that use its options are in a place to efficiently put together for audits, resolve incidents quicker to allow them to limit downtime and streamline utility deployment. Because of the elevated reliance on the cloud, cloud security specialists are in excessive demand and can remain so in the future. The role of a cloud safety specialist is to protect information, techniques, and networks from cyber-attacks. They do this by analyzing threats and vulnerabilities, implementing safeguards, monitoring networks for intrusions, and overseeing compliance with laws. With the increase in the technology of digital information, it is anticipated that cyberattacks will quadruple shortly. This proves that growth in the variety of cyber safety jobs will solely enhance as organizations will want professionals who can guarantee information safety.
Cloudflare serves businesses of all sizes, nonprofit organizations, humanitarian teams and governments worldwide. Customers can also purchase answer and consulting providers and complete safety coaching. Rapid7 specializes in cybersecurity and information analytics, offering merchandise corresponding to vulnerability administration, software safety, IT operations, penetration testing and extra. The company also provides a variety of technology and consulting services, and just lately announced new generative synthetic intelligence (AI) capabilities. Cybersecurity Architects are answerable for designing, building, and overseeing the implementation of a corporation’s cybersecurity infrastructure.
The problem that many individuals have is that they don’t understand how finest to discover and harvest this knowledge. OSINT investigators have the talents and resources to discover and procure data from sources all over the world. They assist people in different areas of cybersecurity, intelligence, navy, and enterprise. The CISO leads workers in figuring out, creating, implementing, and maintaining processes throughout the group to scale back data and knowledge expertise dangers. CISOs respond to incidents, establish applicable requirements and controls, handle security technologies, and direct the establishment and implementation of policies and procedures.
